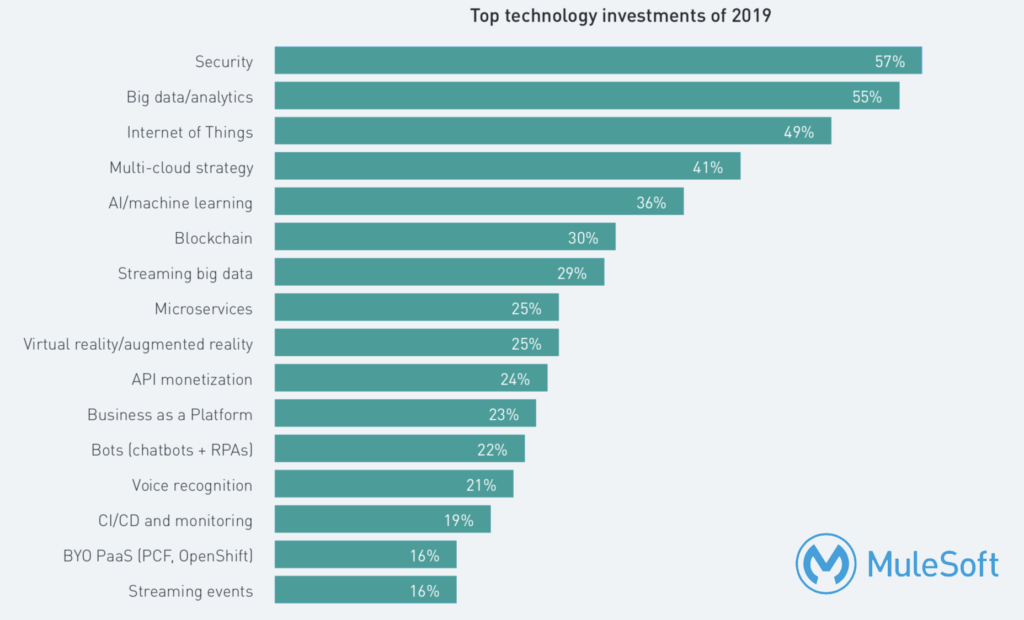
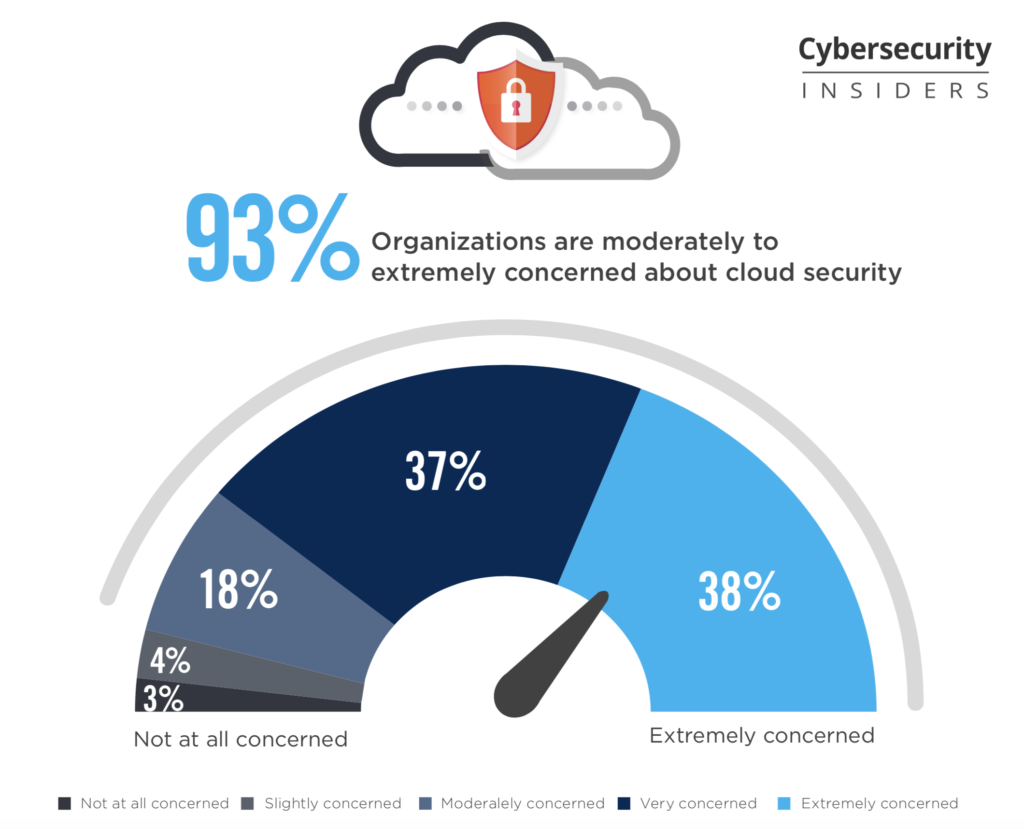
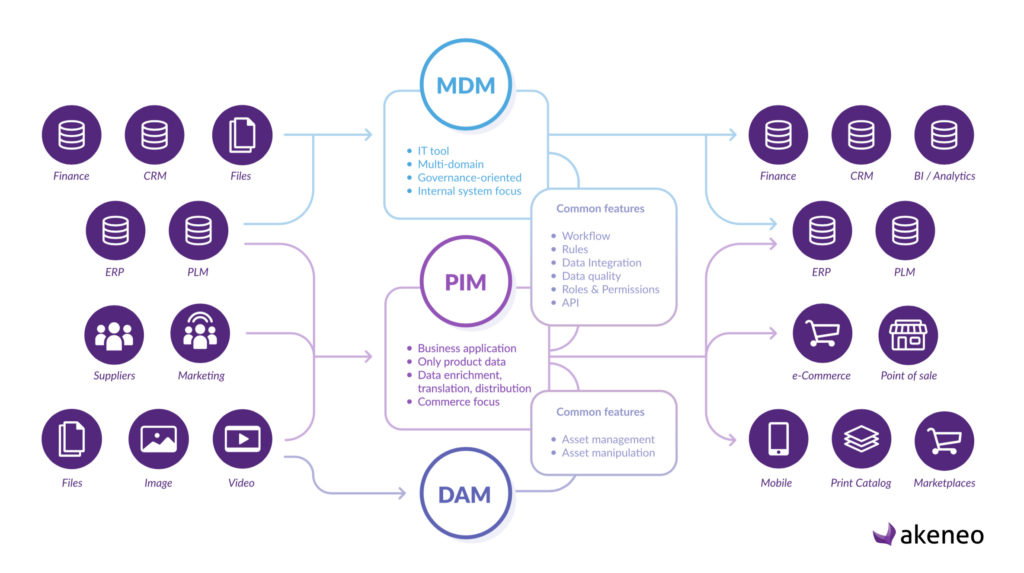
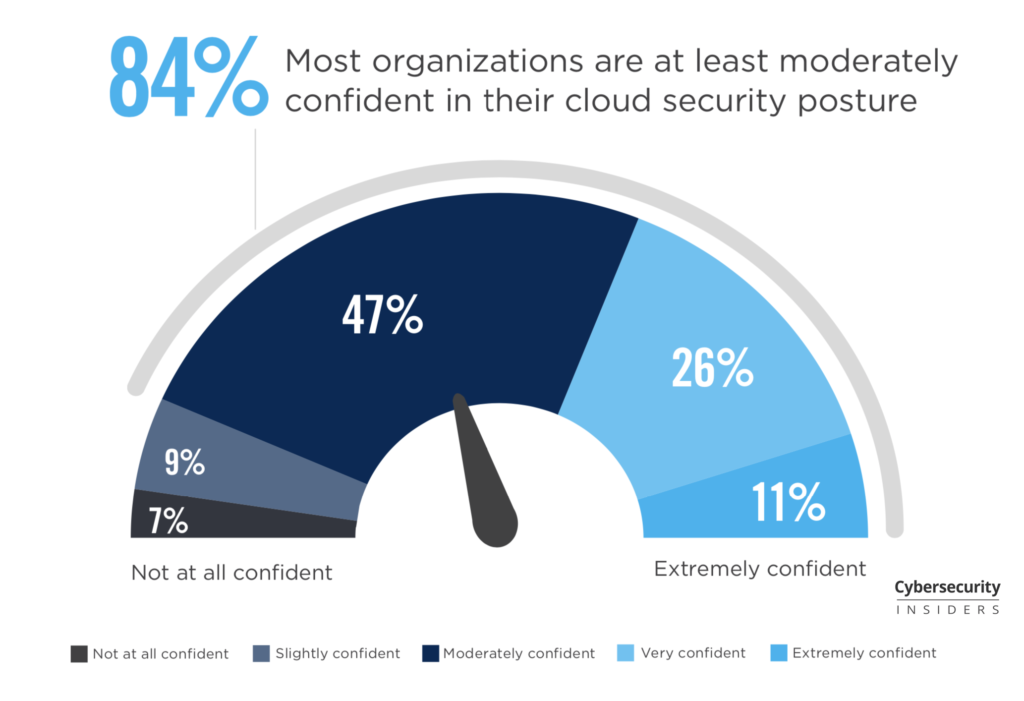
Security is now at the top of customers priority like unveiled by the survey of Mulesoft or exposed by Forbes (The 5 Biggest Cybersecurity Trends In 2020 Everyone Should Know About).
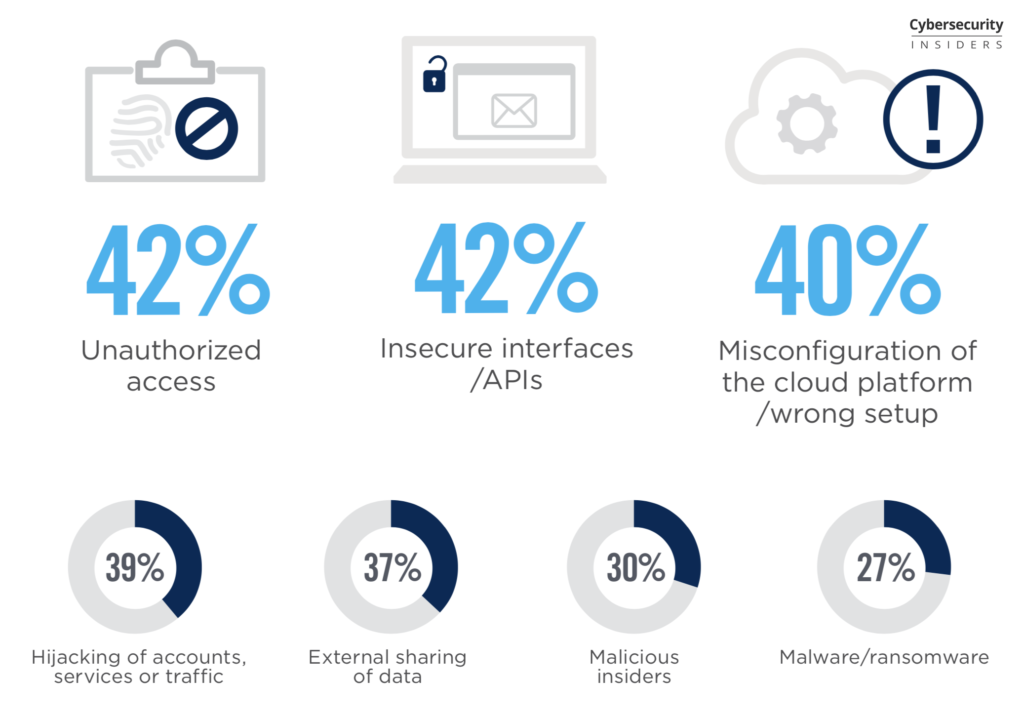
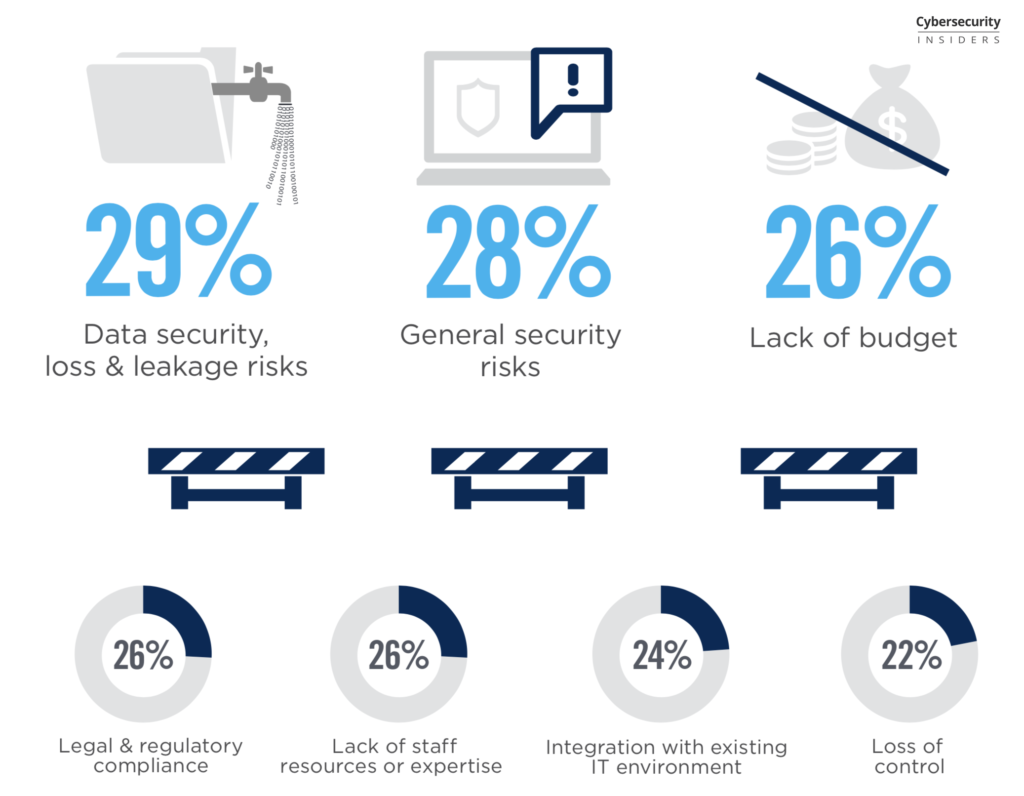
93% of organizations are extremely concerned about cloud security. During the last years Cloud continues to rise and today more than 85% of DAM systems are cloud based. Yes it involves more concerns with your data loss, unauthorized access, misconfiguration or bugs, encryption and more. But how organizations adapt to these cloud security challenges will be interesting in 2020.
It is always a challenge to give predictions on this topic and most experts predict a rise in misconfiguration leading to more breaches, while others look to new SaaS solutions and alliances to move the market forward.
Look at the great cloud security report and analysis from Cybersecurity Insiders
When we are thinking about the brand consistency along side the customer experience, the foundation of technology marketing stacks often starts from a DAM system to organise all the digital content in a unique source of content and a PIM system to drive the data for the business lines.
From the asset creation to the distribution on all the communication channels (social, websites, ecommerce) it is important to maintain the consistency of the brand but above all the main requirement of consumers even after the customer experience of the solution is the security for 2 main reasons :
- more then 80% of solutions avec cloud based and even if DAM and PIM vendors are relying their solutions on AWS Amazon, Azure Microsoft or Google it doesn't mean that they are supporting and manage the security of the application
- Since a couple of years the framework of solutions has moved to new web frameworks (Angular, React etc…) driven by APIs. It is a good step forward the user interface, responsive and easy to use reaching a new level of customer experience but it is also new threats for the customer.
Cyber Security :
During my last trade show and conferences it was interesting to see how the enterprise DAM community was managing cyber security and threat protection. Most of vendors are claiming either a cloud or hybrid offerings. It’s getting very cloudy and everyone thinks that solves all the issues – NOT!
Too many times vendors are saying “it’s not really an issue because we are in the cloud and browser accessed”. While we all want to believe the cloud providers are doing an excellent job in security, we forget that getting to the cloud or from the cloud from an endpoint (Computer, Tablet or smartphone) is typically over an open Internet connection. Going to the cloud is also a risk for your brand if you are not checking some basic requirements on the vendors side. Hopefully most IT departments have a good processes to challenge them.
Vulnerability Questions :
Most of Internet Browsers are very vulnerable connections and expose the digital content to threats. Most of the assets are created on the endpoint, interacting with removable media or attached storage or downloaded from another web service. Most enterprises are using network and endpoint threat protection, and care using web scanning for any online services or products. So the big question is how DAM systems are managing the protection during the ingest ? Some DAM are offering http connexion with third cloud services, streaming and live content or http assets links ? It exposes the DAM to treats. While cloud service providers like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) continue to expand security services to protect their evolving cloud platforms, it is ultimately the customers’ responsibility to secure their data within these cloud environments.
Hopefully some vendors cloud based have initiatives working to address this issue based on those treats :
- Identify security breaches affecting the application and exploitable by hackers connected to the Internet
- Assess the level of security of the application against threats from the Internet
- Identify the security breaches affecting the application and exploitable by its own authenticated users
- Assess the level of security of the application against threats from its own authenticated users
- Measure the gap between the adequate security level and the security level implemented
- Propose an action plan to improve the security level of the application and to remedy the identified vulnerabilities
- Database injection
- Cross Site Scripting
- Insecure direct object reference
- Access control and privileges
- File upload exposure
- HTML injestion
- Javascript issues
- Unsecured redirects
- Network scan
Just like we have DAM scenarios to stamp the vendors this is the good path to consider security attack scenarios.
So reason why it is a good best practice to do some application penetration tests with the solution.
The application penetration tests have too be carried out according to a sequential approach inspired by the good practices described in the ISO 27002 standard, the OWASP and the PTES. The steps of the process are :
- Information gathering (Collection of information relating to the web platform and analysis of the application workflow)
- Identification of "pre-authentication" vulnerabilities (Determination of "pre-authentication" vulnerabilities affecting the application)
- Identification of "post-authentication" vulnerabilities (Determination of "post-authentication" vulnerabilities affecting the application)
- Penetration (Exploitation of detected vulnerabilities)
Most companies have a reactive approach to security, acting only when they are attacked. In an interconnected environment such as digital asset management, it is extremely important to actively monitor the network for threats, be it insider or external attackers. Any IT departments should be able to configure baseline security protocols across the data environments. Complying with regulations such as PCI-DSS and GDPR is a must for companies working across geographically distributed environments.
Coming back to the DAM maturity model, it should be more than welcome from committees and trade organizations to put effort into protecting the operating environment and the digital content managed by the DAM system ?
Artificial Intelligence as Security Solution ?
Innovation around AI and ML can help to accelerate identification of and response to these threats, especially the latest ones. AI-enabled security tools and products can detect and respond to cybersecurity incidents with minimal or zero input from humans. But in the same time, hackers are also using the same technology to get knowledge from AI. Definitely AI will play a main role to protect DAM systems outside of basic images recognition. AI will automate detection and response processes but it is also a double-edged sword that can be also used as a weapon by hackers.
Some ISO standard like the 27001 are providing requirements for an information security management system (ISMS), a risk management framework of policies and procedures for managing sensitive company information that an organization collects, stores, transmits or processes from customers. More and more vendors are adopting the standard, a good sign for customers to keep their data and digital content safe.
To end up I will also highlight DRM technologies to your assets as I was writing in a post lasts year . Like Imatag proving technologies to monitor your assets and to prevent brand erosion, detect unauthorized usage, and calculate earned media.
If you have to start any DAM PIM CMS project, contact us to select the right solution, with a great customer experience but also the top security regarding your business requirements with the best ROI.
Frédéric SANUY